LWN.net Weekly Edition for February 26, 2009
Fedora looks to increase Rawhide testing
Development branches of a distribution are generally hard environments to use because they tend to frequently be in a broken state—so broken that it is impossible to get one's work done. Fedora Rawhide is such a branch, which, up until recently at least, came with the scary warning: "Rawhide eats babies". So it is a bit surprising to see an effort to increase the number of Rawhide users. The benefits for Fedora are obvious, but the number of headaches and complaints that could come from more users might offset the extra testing that it would get.
Rawhide horror stories abound, but, in general, its quality has been
improving in recent times. As part of a report from his recent orientation
at Red Hat headquarters, Adam Williamson posted some goals for Fedora QA to the
fedora-testers mailing list. The first specific goal listed—and the
one that attracted most of the comments on his post—was to
"increase participation in Rawhide
". Williamson was formerly
a community liaison with Mandriva and recently took on a similar role in QA at
Red Hat. He outlined some specific steps that the QA group wants to take
with Rawhide:
Mark McLoughlin suggested coming up with some criteria for what a testable ("dogfoodable" in his words) Rawhide looks like. Changes that cause it to fall below that line—because it doesn't boot or some core functionality, like networking or graphics, doesn't work—should be added to bugzilla as a RawhideBlocker bug. Pressure could then be applied to get those bugs fixed quickly. Interested testers would also have an opportunity to see if Rawhide was in a testable state before installing or updating.
Concerns were expressed about just who should be considered a good
candidate for testing Rawhide. McLoughlin thinks "we should keep
trying out new things to
get it to the stage that anyone involved in Fedora development should be
able to run rawhide
". Williamson agrees:
But Bruno Wolff is worried that the bar is being set
too low: "you need to be able to rescue your system when booting
fails.
I think you pretty much need to be an amateur sysadm.
" Williamson,
based at least partially on his Mandriva experiences, is not too worried about that problem:
It is clear that one can run into problems with Rawhide, but the author was able to write the bulk of this article—along with handling a few other normal tasks—on a laptop running Rawhide from February 24 with few problems. The display would not default to the 1280x800 resolution of the laptop—likely caused by bug 485913—but that could be worked around by use of the KDE display setting program. Wolff also reported some nasty boot problems and alluded to kernel modesetting issues both of which would be problematic for a regular user to overcome. Some grumpy guy from LWN, who often runs on the bleeding edge, pointed out a few other issues (with tomboy, cups, and others) that he has run into using Fedora 11 Rawhide.
But, the only kind of testing that is likely to find these kinds of problems is real-world day-to-day use of the distribution—a quick install test won't show them. It is the classic chicken-or-egg problem that distributions face. Most distributions opt for recommending that users stay away from their development branches, instead awaiting alphas, betas, or release candidates. Finding critical bugs at that point is much more painful, however. Fedora is trying to find a middle ground between getting buried in bug reports, while still finding bugs as early as possible in the process.
Each user has their pain threshold that they are willing to bear while helping to improve the free software they use. Some have a threshold near zero, while others have enough experience—or masochism—to be willing to deal with the kinds of messes that can result from tracking a development branch. It is best for all concerned to make sure that the right message is sent, so that the right people are using Rawhide. If expectations are not set correctly, it could well leave Fedora worse off than it was before. It is an interesting experiment, one worth keeping an eye on.
The trouble with OpenBTS
Last September, LWN pointed out the OpenBTS project, which is working toward the creation of a free GSM base station using GNU Radio and Asterisk. OpenBTS had just been demonstrated through the creation of a cellular network at Burning Man. More recently your editor, who had been looking in other directions, was surprised to learn that the OpenBTS developers are not allowed to tell anybody where to get the source from, despite the fact that it is available as free software. Intrigued, your editor decided to look into what is happening with OpenBTS.OpenBTS is clearly an interesting project; who wouldn't like the potential of rolling their own cellular phone service? There are a number of potential applications, including special events like Burning Man, the creation of personal "femtocells," or the ability to explore how cellular handsets interact with base stations. The biggest target application, though, would appear to be the provision of inexpensive cellular service in parts of the world where the cellular industry sees no money to be made. In the rural parts of the developing world, potential customers simply cannot afford to pay normal cellular rates, and carriers fear that low-cost offerings, beyond being unprofitable, would endanger the higher rates charged in the cities. Using systems like OpenBTS, cheap hardware, and some interesting business models, it may well be possible to bring phone service into these areas in a way which is simultaneously affordable and acceptable to the large carriers.
So what is the problem with OpenBTS? One might think that an obvious trouble spot would be regulatory: spectrum for cellular services tends to be scarce and expensive. It is true that one cannot set up an OpenBTS station in the attic and expect to be left alone, but it also seems that the regulatory issues can often be dealt with, especially in places where cellular coverage does not exist. The real issues come from a different, all-too-familiar direction: "intellectual property" law.
When LWN first wrote about OpenBTS, the source code was not yet available. On October 24, 2008, the OpenBTS developers formally donated this code to the Free Software Foundation, putting it under the GPLv3 license in the process. OpenBTS is now part of the GNU Radio project. There has not yet been a GNU Radio release which includes OpenBTS, but interested parties can learn about it - and find out how to check out the current code repository - from the OpenBTS wiki on the GNU Radio site.
The transfer of the copyrights was the result of a direct intervention by John Gilmore, who, while certainly being motivated by the opportunity to improve GNU Radio, also likely saw the potential for trouble in the near future. The problem is that David Burgess, the primary author of the OpenBTS code, previously did GSM-oriented work for a company called Martone Radio Technology, Inc. Massimiliano Martone, the owner of this company, filed suit against David, alleging that the OpenBTS code contains Martone's proprietary information. David denies these charges, stating that GSM is documented in a series of open standards and, thus, cannot be proprietary. See this filing [PDF] for a lot of details about the history of the OpenBTS code, this case, and David's defense.
Whether this defense will hold remains to be seen; this case is pending as of this writing. The judge did, however, issue a preliminary injunction reading:
This is why nobody associated with Kestrel Signal Processing (David's company) can say anything about where the code is located. However, David does not own this code; the FSF owns it, and the FSF is not a party to this particular dispute. So the FSF is not subject to this injunction. The FSF is also uninclined to collect information on people who download its code. So the OpenBTS code remains available for anonymous download, this injunction notwithstanding. If Martone is able, somehow, to convince a judge that it has some claim on that code then the situation could change, but, for now, obtaining OpenBTS is possible - though Kestrel is not able to contribute any further changes to the FSF version.
There is, however, another issue that potential OpenBTS users need to be aware of. While the GSM standard is "open," in that it is publicly available, it is not a free standard; many parts of it are encumbered by patents. So anybody who wants to set up a production GSM base station powered by OpenBTS (or anything else, for that matter) must have acquired patent licenses from the various owners. Given that, one might wonder how the code can be distributed; David has posted an explanation on his weblog. It comes in two parts, the first of which is:
In other words, the FSF is distributing code with known restrictions on its use; this is a bit of a change for an organization which is not normally enamored of software which is only available for "private experimental use." But, evidently, this approach makes it possible to put the code out there under the GPL.
But, even if one accepts this reasoning, there is another problem to face: the GPLv3 text contains some strong language designed to protect users against patent problems. Anybody who (1) has the patent licenses necessary to actually deploy OpenBTS, and (2) contributes to or distributes the OpenBTS code must arrange for recipients to obtain the same patent protection. Needless to say, that is not really an option in this case; the owners of these patents (companies like AT&T, Ericsson, and Alcatel) have not expressed any great willingness to license them to OpenBTS users. So the only people who can distribute OpenBTS are, in general, those who can't actually make use of it. In other words, it would appear to be impossible to use OpenBTS in a commercial product in a way which satisfies both the patent requirements and the GPLv3 requirements.
Quoting David again:
The specific GPLv3 text being referred to would appear to be section 6d, which reads, in part:
So, as long as somebody is distributing OpenBTS without their own modifications, and they do not, themselves, hold licenses to the GSM patents, they need only point to the GNU Radio repository. This assumes that the operator of that repository is committed to making the source available for the requisite period of time - probably a good assumption when that operator is the FSF. That said, this is a fairly intricate dance designed to get around, in some sense, the patent licensing requirements of GPLv3.
And that is where things stand at the moment. In OpenBTS, we have a software platform which could be used to, among other things, bring affordable telephone service to large numbers of people who have no such service now. This code has been written to conform to published standards which are in use worldwide, and it has been freely licensed under GPLv3. Thanks to the current legal climate, though, this code currently has an uncertain future, a future which must certainly weigh on the minds of anybody considering making use of it.
SCALE7x: Courts have new "teeth" to limit software patents
A surprising decision from the second-highest court for US patent cases will put meaningful restrictions on the patentability of software here, Red Hat patent lawyer Rob Tiller said in a well-attended talk at the Southern California Linux Expo. In a surprise October ruling in the case of In re Bilski last year, the Court of Appeals for the Federal Circuit "threw out wholesale" the existing test for software patentability, and substituted a new, stricter one. "The test has teeth," said Tiller, who, as Vice President and Assistant General Counsel, IP for Red Hat, handles incoming patent threats and authored an amicus brief in the case.
The patent at issue was a business method for hedging
commodities transactions; the Federal Circuit
found the method unpatentable under a new test:
in order to be patentable, a process must be either
tied to a particular machine or apparatus, or must
transform a particular article into a different state
or thing. However, the court, "left to future cases
the elaboration of the contours of the test," Tiller
said. The Federal Circuit threw out its previous
standard, which it set in the State Street Bank
& Trust Co. v. Signature Financial Group, Inc.
case in 1998. That decision, which opened the door
to pure business method patents, allowed a patent
on a mutual fund business method under a "useful,
concrete and tangible result" test. In the Bilski decision [PDF],
the Federal Circuit's chief judge, Paul R. Michel,
wrote, "those portions of our opinions in State
Street and AT&T relying solely on a 'useful, concrete
and tangible result' analysis should no longer be
relied on.
"
Questions remain about what kind of machine is
"particular" enough. Will a patent applicant need
to affect a real event outside the computer, such as
the timing of a rubber-curing machine, or is moving
electrons within a general-purpose computer enough?
"This is something that courts and patent attorneys
are scratching their heads about," Tiller said later.
It's possible that a software-patent-friendly
interpretation of Bilski could simply include a
"general-purpose computer" in a patent claim, and
trivially get around the requirement for a particular
machine or apparatus. But, Tiller said, "It's hard
to argue that a general purpose computer alone will
suffice." Judge Pauline Newman wrote in dissent,
"For the thousands of inventors who obtained patents
under the court's now-discarded criteria, their
property rights are now vulnerable.
"
"Bilski suggests that the Federal Circuit believes the Supreme Court is concerned with its work," Tiller said. In an unusual move, the Federal Circuit heard the case en banc, with all twelve judges involved, instead of in a smaller panel. Nine agreed on the ruling, with two against the new test and one dissenter writing that the court didn't go far enough. "They really are concerned that if you grant too much patent protection you could inhibit innovation," Tiller said. In the Red Hat amicus brief, Tiller summarized the often-heard economic arguments against software patents, and argued that the State Street test was inconsistent with the Supreme Court's previous patent decisions.
In a 1972 case, Gottschalk v. Benson, the Supreme Court ruled that an algorithm for converting binary-coded decimal data to binary was not patentable. Later, in a 1981 decision in the case of Diamond v. Diehr, the Supreme Court decided that a process for curing rubber that includes a computer-implemented algorithm is patentable. The Red Hat amicus brief says, "Diehr reaffirms that abstract ideas by themselves are unpatentable, and that only inventions that are sufficiently tangible are patentable."
The patent holder has requested that the Supreme Court hear the Bilski case, but the Supreme Court accepts few such requests, Tiller said. Groklaw covered the Bilski case thoroughly (Part 1, Part 2, Part 3) and called it "The End for the stupidest of the stupid patents."
Tiller got an easy round of applause when an audience member thanked him for Red Hat's refusal to sign a dubious patent agreement with Microsoft, as Novell did. Although Red Hat did not give ground to Microsoft's patent threats, Microsoft blinked first and agreed to establish virtualization interoperability agreements with Red Hat without a Red Hat signature on a patent shakedown.
Tiller also asked for some policy changes to ease the patent stress on the software business. "Since 1994, US litigation costs have substantially exceeded profits from patents," he said, except in the chemical and pharmaceutical industries. "If we can't have a subject matter exclusion for software, is there anything else that can be done?" he asked. Improving patent search tools would help, and requiring source code with a patent application would make it easier for working software developers to identify problem patents, since it's easier for them to read code than the tortured language of patent claims. An independent invention defense would also help, he said. "We ought to carve out the situation where a second inventor, just as creative but a little later, comes up with the same invention," he said. Senator Patrick Leahy of Vermont plans to re-introduce a bill to reform patent damages and reexamination requirements, Tiller said. "We in fact supported that bill."
Linux users can help with the patent problem. "Talk about this problem. Educate ourselves and educate others. Instead of fostering innovation it's hindering innovation," he said. "We have a large amount of work to do to educate people about this." Red Hat is also seeking prior art to help defend a lawsuit from a patent troll firm that is suing both it and Novell.
SCALE7x: Open source in an economic downturn
If you work with open source software, you have less to worry about in the current economic downturn, according to John Todd of Digium — the company behind the Asterisk telephony platform. Todd presented his ideas at SCALE in Los Angeles, arguing that many of the same factors that put jobs and revenue at risk in the proprietary software industry actually benefit open source projects and, by extension, provide job security for developers, implementers, and consultants who work with open source.
Businesses' motivations to adopt open source software solutions are not affected by hard economic times, Todd said: open source is often the best solution technically, and its well-understood benefits of lower total cost of ownership, flexibility, and customizability are just as real when budgets are flush as they are when budgets are lean. But decision makers focus on many of these factors in a downturn, which benefits open source. Cost becomes a life-or-death factor when the very survival of the business is on the line, he observed, while in better times companies may spend money for other reasons — to please investors, to keep up with appearances, or simply because they have the annual budget and do not want to end the year with a surplus. "Having no money, or the threat of no money, sharpens the mind about cost," Todd concluded.
Furthermore, making the best technical decision becomes more important in lean times, because the downside of being wrong is dire. And, he added, it is a well-known benefit of open source that if you choose an open source solution that turns out to be wrong, you can often code your way out of the problem, but at worst you have lost only time. With a proprietary solution, you cannot fix the problem yourself, and the vendor (under its own budget cuts) is less likely to be responsive to your requests for changes. In the end, you are out both time and money.
The slowing economy will also benefit open source in the increased availability of free resources, Todd said — first and foremost developer time. Laid-off developers continue to code in their spare time, in order to maintain their skills, learn new techniques, and simply because they enjoy it. Open source projects stand to gain from the increased pool of willing contributors along with increased availability of those who already participate in projects after-hours. Some coders leaving the proprietary world may even find jobs at companies that produce or support open source software or find roles in consulting. In addition, with businesses downsizing, surplus hardware equipment and bandwidth becomes available to be snapped up at low cost by both projects and open source companies. The hardware phenomenon happened after the dot com burst, he said, and may be repeated on an even larger scale this time due to the size of the economic recession.
Finally, Todd said, several recent developments make the timing of this recession especially good for open source to take advantage of. Unlike previous recessions, pervasive world-wide Internet, a rapidly-growing and connected open source community, and development tools that match or exceed anything available in the proprietary world are already in place. Although processors become cheaper every year, today virtualization and cloud computing make CPU cycles and storage available to anyone with zero capital expenditure. These factors benefit the open source movement more than they do proprietary companies because they are already integrated into the open source model.
Open source is not magic, Todd concluded. It is successful for well-known and well-understood reasons. But the tough economy reveals one dimension often hidden during more favorable conditions: open source is not vulnerable to the same pressures as proprietary software. No revenue stream is responsible for keeping open source code alive, but when the revenue stops, proprietary code dies. Commercial companies fire developers to cut expenses and must slow down as a result, but open source software continues to improve even when no money is coming in.
As logical as Todd's reasoning is, it was met with a small measure of skepticism from the audience. One listener challenged the assertion that layoffs would mean more spare time for developers to devote to open source coding. Aren't developers working longer hours for the same pay because of short-staffing, he asked? Todd replied that while it was true that many developers who have kept their jobs will find themselves working more hours, those hours are outweighed by the hours freed up by the developers laid off.
Todd concluded his talk by sharing some comments from Asterisk integrators and resellers, some of whom went so far as to deny that there was an economic downturn. They are statistical outliers, perhaps, but because their core business is replacing costly proprietary systems with open source alternatives, they are already "under the shield" of open source. Todd is making his entire presentation [PDF] available under Creative Commons Attribution-Noncommercial terms, and he invites others to contribute to the discussion. Todd's underlying premise is that open source "decouples the developer and what the developer produces from economics." Whatever your opinion on the causes or the future of the current economic recession, it is hard to argue with that proposition.
Microsoft sues TomTom
As seen in this TechFlash article, Microsoft has launched a patent suit against TomTom, a seller of (Linux-based) navigation devices. "It's believed to be the first time Microsoft has filed a patent suit over Linux, after claiming for years that elements of the open-source operating system violate its patents. However, Microsoft says open-source software is not the intended focal point of the action."
The complaint [PDF] is online. The patents involved are 6,175,789 (Vehicle computer system with open platform), 7,054,745 (Method and system for generating driving directions), 6,704,032 (Methods and Arrangements for Interacting with Controllable Objects within a Graphical User Interface Environment Using Various Input Mechanisms), 7,117,286 (Portable computing device-integrated appliance), 6,202,008 (Vehicle computer system with wireless internet), 5,579,517 (Common name space for long and short filenames), 5,758,352 (Common name space for long and short filenames, again), and 6,256,642 (Method and System for File System Management Using a Flash-Erasable, Programmable, Read-only Memory). Stay tuned, it could be interesting.
Security
Desktop malware risk gets raised and patched
One of the most common claims about GNU/Linux is that it is supposed to be relatively immune to viruses and malware. However, for the past few weeks, that claim has been more closely scrutinized, thanks to a blog posting by "foobar" entitled "How to write a Linux virus in 5 easy steps." Specifically, the posting gives a high-level explanation of how malware can take advantage of the behavior of application launchers on the GNOME and KDE desktops to infect a user account — and possibly gain root access as well. The result has been endless Internet discussions and coordinated efforts by both GNOME and KDE to minimize the problem.
The method described by foobar depends on social engineering: That is, manipulating users into saving an attachment to their GNOME or KDE desktop, and then into executing it. Ordinarily, foobar points out, a saved email attachment would not have executable permission. However, GNOME and KDE share a common format for desktop launchers (*.desktop), and allows them to run without an executable flag. This exception makes it easy to run a script (foobar suggests Python as a likely language) that will download a piece of malware, especially since a custom icon and name can disguise the nature of the program that the launcher runs. Furthermore, by adding a link in the desktop environment's autostart directory, the malware can then run each time that a user logs into the account.
From the perspective of security architecture, gaining root access is
considered the goal of malware. However, foobar emphasizes that the method
described can do damage without logging into the root account. Still,
foobar suggests that the use of sudo and temporary root logins for
graphical administration tools provide a backdoor for gaining root
access. According to foobar, all that a piece of malware would need to do
is make a local copy of an administration tool, then run the malware
referencing the local copy. A user would then enter the root password for
the tool, and not notice that the malware command was also receiving root
access. Alternatively, the malware could add a similar command to the path
definition of the current account. Either way, foobar writes,
"there's a good chance that you will get [root access] eventually if
you are patient.
"
These suggestions are not new. LWN pointed out the basic problem nearly three years ago, and the potential vulnerabilities of sudo were pointed out two years ago in an Ubuntu forum. All the same, foobar's post has been widely discussed since it first appeared. Besides the comments below the post, it has been discussed in such places as Linux Today, LWN, Slashdot, the KDE Community Forums, and the Ubuntu Forums.
Much of this discussion is repetitive, and beside the point. For example,
some users quibble that foobar is technically referring to a trojan, not a
virus at all. Others, like "Felice" below the original post, dismiss
foobar's analysis on the grounds that, "There will never be any
protection against the user's stupidity.
" Others, like "friends of
the one law" (also beneath the original post) insists that such exploits
are less likely on GNU/Linux than on Windows because "The
installation and/or maintenance of a basic linux desktop requires a level
of knowledge _and_ intellect somewhat more developed than that required for
a basic Micro$oft product.
" All these comments, however, are side
issues that do not alter the basic problem in any way, even though they
each contain some degree of truth.
Other comments were more to the point. Expanding on a comment by foobar, "Colin" posted beneath the original post with a link to the code snippet that prevents Thunar, the Xfce file manager, from having the same desktop vulnerability. Still others tried to correct foobar's suggested code or variations on the basic method outlined.
Some of the most focused responses appeared as comments to LWN's initial coverage of the story. "drag" suggested using a tool like SELinux to create a security context for downloads to the desktop that flags them as untrusted until they are specifically marked as trusted. The same commenter suggested that downloads should be savable only to a designated directory off the desktop — although, as foobar pointed out in the followup blog post, whether this idea would work is uncertain.
In the last few days, both GNOME and KDE have been taking concrete steps to
alleviate the problem, with discussions taking place on the XDG
(Free Desktop) list. In a blog
post, Michael Pyne proposes a policy that will allow files with a .desktop
extension to run if they are owned by root (and therefore part of a
standard installation), or installed from "a known location for
services, applications, and XDG-compliant applications
" (that is,
ones that meet the shared Free Desktop standards). A whitelist will track
all .desktop files that are permitted to run.
Pyne tells LWN that a major challenge of implementation is getting the white list correct. His first whitelist excluded autostart entries, and discussion raised a number of other cases, such as whether existing .desktop files needed to be updated, and how to handle launchers created from a menu or panel.
Another issue raised on the XDG list is whether a header should be added to untrusted .desktop files to prevent them from being run from the command line. While some developers questioned the need, Pyne seems to have decided that the precaution is necessary.
Still another concern is to write a clear dialog window that opens when a user tries to launch a .desktop file that is not whitelisted and is therefore not executable. The language is still being improved, but will probably explain the potential danger and when you should and should not continue to run the program, as well as giving the complete path to the command.
GNOME developer Alexander Larsson, although writing that the issue is
"all
pretty overblown,
" is working along similar lines. When the
changes are implemented, GNOME will add an executable permission to all
existing .desktop files when upgrading — a move that KDE, for now,
will not follow. "We thought about it but opted to start with the
dialog,
" Pyne tells LWN. "Some kind of dialog will be required
no matter what, and any auto-upgrade we do in KDE would have to be done
with the user's permission. We may still do it, but it not set yet.
"
Another difference in GNOME is that any .desktop files that are executable but not in a system directory will be flagged as "untrusted." To emphasize their status, such files will show a shortcut icon and the real file name, rather than any custom icon and display name for the desktop. Pyne has expressed some interest in this idea to LWN, and briefly speculated about how files might be listed as trusted, but, for now KDE is not following this suggestion.
However, much as in KDE, clicking an untrusted file in GNOME will open a dialog that warns the user about the file's status, and gives the choice of running it anyway, marking it as trusted, or canceling its execution.
In both GNOME and KDE, these changes should appear very shortly. Larsson
asked for a string break approval
for next month's release of GNOME 2.26 so that his changes, particularly
the new dialog, can be included. The request was granted, and Larsson tells
LWN, "all the required Gnome changes have now landed in glib and
nautilus.
"
Similarly, Pyne hopes to see his changes backported to KDE 4.2 in a point
release, as well as appearing in KDE 4.3. Whether the backports occur, he
explains to LWN, depends "on if it's deemed a big enough security
risk.
"
The speed with which these changes are being implemented suggests that both KDE and GNOME are treating the security problem as moderately serious. However, Pyne is careful to warn about the limits of the fixes, telling LWN:
In other words, the fixes should minimize the chances of a malware infection of the type describes by foobar, but, as many commenters have pointed out, nothing can completely counter user ignorance, rashness, or plain stupidity. The most that desktop developers can do, short of restricting desktop files to a degree that most users would find unacceptable, is to make users aware of the consequences of their possible actions.
Brief items
OpenSSH 5.2 released
OpenSSH 5.2 has been released with a focus on bug fixes. In particular, it addresses the plaintext recovery attack described in CPNI-957037 (which LWN covered last November). "This release also adds countermeasures to mitigate CPNI-957037-style attacks against the SSH protocol's use of CBC-mode ciphers. Upon detection of an invalid packet length or Message Authentication Code, ssh/sshd will continue reading up to the maximum supported packet length rather than immediately terminating the connection. This eliminates most of the known differences in behaviour that leaked information about the plaintext of injected data which formed the basis of this attack. We believe that these attacks are rendered infeasible by these changes." Click below for the full release announcement.
The Cryptography Olympics : the hash algorithm contest (The H)
"The H" is the new name for heise online and it takes a look at the currently running competition for a next-generation cryptographic hash algorithm. "The impetus for the cryptography competition was provided by the cracking of existing security standards by various researchers. Such attacks serve to probe protection mechanisms and aid their development. Because the world needs reliable protection, the National Institute of Standards and Technology (NIST), part of the U.S. Department of Commerce, issued the call for an international Cryptographic Olympics. The victorious algorithm must [fulfill] the full range of requirements imposed by data processing technology, ranging from sensors the size of a grain of sand, to future high speed data networks."
New vulnerabilities
epiphany: arbitrary code execution
| Package(s): | epiphany | CVE #(s): | CVE-2008-5985 | ||||||||||||||||
| Created: | February 23, 2009 | Updated: | March 9, 2009 | ||||||||||||||||
| Description: | From the Mandriva advisory: Python has a variable called sys.path that contains all paths where Python loads modules by using import scripting procedure. A wrong handling of that variable enables local attackers to execute arbitrary code via Python scripting in the current Epiphany working directory | ||||||||||||||||||
| Alerts: |
| ||||||||||||||||||
git: arbitrary code execution
| Package(s): | git | CVE #(s): | CVE-2008-5916 | ||||||||
| Created: | February 19, 2009 | Updated: | March 9, 2009 | ||||||||
| Description: | git has an arbitrary code execution vulnerability. From the vulnerability database entry: gitweb/gitweb.perl in gitweb in Git 1.6.x before 1.6.0.6, 1.5.6.x before 1.5.6.6, 1.5.5.x before 1.5.5.6, 1.5.4.x before 1.5.4.7, and other versions after 1.4.3 allows local repository owners to execute arbitrary commands by modifying the diff.external configuration variable and executing a crafted gitweb query. | ||||||||||
| Alerts: |
| ||||||||||
kernel: various issues
| Package(s): | kernel | CVE #(s): | |||||
| Created: | February 20, 2009 | Updated: | February 25, 2009 | ||||
| Description: | From the Mandriva advisory: Support was added for Intel 82567LM-3/82567LF-3/82567LM-4 network adapters, a bug in sunrpc causing oops when restarting nfsd was fixed, a work around for a bug in Walkman devices was added, the sound drivers got some fixes, and a few more things were fixed. Check the package changelog for details. | ||||||
| Alerts: |
| ||||||
libpng: arbitrary code execution
| Package(s): | libpng | CVE #(s): | CVE-2009-0040 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Created: | February 23, 2009 | Updated: | July 13, 2009 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Description: | From the SecurityFocus advisory: The 'libpng' library is prone to multiple memory-corruption vulnerabilities because it fails to properly initialize data structures. Successful exploits may allow remote attackers to cause denial-of-service conditions or potentially execute arbitrary code on computers running the affected library. These issues affect versions prior to 'libpng' 1.0.43 and 1.2.35. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Alerts: |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
perl-Crypt-OpenSSL-DSA: improper error check
| Package(s): | perl-Crypt-OpenSSL-DSA | CVE #(s): | CVE-2009-0129 | ||||||||
| Created: | February 19, 2009 | Updated: | February 25, 2009 | ||||||||
| Description: | The Perl Crypt-OpenSSL-DSA module misses an error. From the Fedora alert: The Crypto::OpenSSL::DSA module now croaks upon error rather than returning a -1 to ensure programmers are not caught by surprise which only checking for non-zero results. | ||||||||||
| Alerts: |
| ||||||||||
php: remote file inclusion vulerability
| Package(s): | php | CVE #(s): | CVE-2009-0577 | ||||||||
| Created: | February 19, 2009 | Updated: | February 25, 2009 | ||||||||
| Description: | php has a remote file inclusion vulerability. From the vulnerability database entry: PHP remote file inclusion vulnerability in function.inc.php in ACGVclick 0.2.0 and earlier allows remote attackers to execute arbitrary PHP code via a URL in the path parameter. | ||||||||||
| Alerts: |
| ||||||||||
php: arbitrary file overwrite
| Package(s): | php | CVE #(s): | CVE-2008-5625 | ||||||||||||||||
| Created: | February 23, 2009 | Updated: | February 23, 2010 | ||||||||||||||||
| Description: | From the CVE entry: PHP 5 before 5.2.7 does not enforce the error_log safe_mode restrictions when safe_mode is enabled through a php_admin_flag setting in httpd.conf, which allows context-dependent attackers to write to arbitrary files by placing a "php_value error_log" entry in a .htaccess file. | ||||||||||||||||||
| Alerts: |
| ||||||||||||||||||
pycrypto: arbitrary code execution
| Package(s): | pycrypto | CVE #(s): | CVE-2009-0544 | ||||||||||||||||||||||||||||||||
| Created: | February 23, 2009 | Updated: | May 13, 2009 | ||||||||||||||||||||||||||||||||
| Description: | From the Mandriva advisory: A vulnerability have been discovered and corrected in PyCrypto ARC2 module 2.0.1, which allows remote attackers to cause a denial of service and possibly execute arbitrary code via a large ARC2 key length. | ||||||||||||||||||||||||||||||||||
| Alerts: |
| ||||||||||||||||||||||||||||||||||
trickle: local code execution
| Package(s): | trickle | CVE #(s): | CVE-2009-0415 | ||||||||
| Created: | February 25, 2009 | Updated: | February 25, 2009 | ||||||||
| Description: | The trickle bandwidth shaper can be fooled into loading arbitrary local code. | ||||||||||
| Alerts: |
| ||||||||||
vim: arbitrary code execution
| Package(s): | vim | CVE #(s): | CVE-2009-0316 | ||||||||
| Created: | February 23, 2009 | Updated: | February 25, 2009 | ||||||||
| Description: | From the Mandriva advisory: Python has a variable called sys.path that contains all paths where Python loads modules by using import scripting procedure. A wrong handling of that variable enables local attackers to execute arbitrary code via Python scripting in the current Vim working directory | ||||||||||
| Alerts: |
| ||||||||||
Page editor: Jake Edge
Kernel development
Brief items
Kernel release status
The current 2.6 development kernel is 2.6.29-rc6, released on February 22. The list of changes is still pretty long, but, with luck, the problems are getting fixed. See the announcement for the short-form changelog, or see the full changelog for all the details.As of this writing, a few dozen post-rc6 patches have found their way into the mainline repository. They include more fixes, but also new drivers for Atheros L1C gigabit Ethernet adapters and FireDTV IEEE1394 adapters.
The current stable 2.6 kernel is 2.6.28.7, released (without announcement) on February 20. It contains the usual long list of fixes, many of which are for the ext4 filesystem; the changelog has the details. 2.6.27.19 was also released on the 20th without an announcement; see the changelog for the list of patches included there.
Kernel development news
Quotes of the week
But we don't do that, because userspace is hard, because we don't have a delivery process. But nobody has even tried!
Speeding up the page allocator
It is a rare kernel operation that does not involve the allocation and freeing of memory. Beyond all of the memory-management requirements that would normally come with a complex system, kernel code must be written with extremely tight stack limits in mind. As a result, variables which would be declared as automatic (stack) variables in user-space code require dynamic allocation in the kernel. So the efficiency of the memory management subsystem has a pronounced effect on the performance of the system as a whole. That is why the kernel currently has three slab-level allocators (the original slab allocator, SLOB, and SLUB), with another one (SLQB) waiting for the 2.6.30 merge window to open. Thus far, nobody has been able to create a single slab allocator which provides the best performance in all situations, and the stakes are high enough to make it worthwhile to keep trying.While many kernel memory allocations are done at the slab level (using kmem_cache_alloc() or kmalloc()), there is another layer of memory management below the slab allocators. In the end, all dynamic memory management comes down to the page allocator, which hands out memory in units of full pages. The page allocator must manage memory without allowing it to become overly fragmented; it also must deal with details like CPU and NUMA node affinity, DMA accessibility, and high memory. It also clearly needs to be fast; if it is slowing things down, there is little that the higher levels can do to make things better. So one might do well to be concerned when memory management hacker Mel Gorman writes:
As might be expected, Mel has come up with a set of patches designed to speed up the page allocator and do away the the temptation to try to work around it. The result appears to be a significant cleaning-up of the code and a real improvement in performance; it also shows the kind of work which is necessary to keep this sort of vital subsystem in top shape.
Mel's 20-part patch (linked with the quote, above) attacks the problem in a number of ways. Many of them are small tweaks; for example, the core page allocation function (alloc_pages_node()) includes the following test:
if (unlikely(order >= MAX_ORDER))
return NULL;
But, as Mel puts it, no proper user of the page allocator should be allocating something larger than MAX_ORDER in any case. So his patch set removes this test from the fast path of the allocator, replacing it with a rather more attention-getting test (VM_BUG_ON) in the slow path. The fast allocation path gets a little faster, and misuse of the interface should eventually be caught (and complained about) anyway.
Then, there is the little function gfp_zone(), which takes the flags passed to the allocation request and decides which memory zone to try to allocate from. Different requests must be satisfied from different regions of memory, depending on factors like whether the memory will be used for DMA, whether high memory is acceptable, or whether the memory can be relocated if needed for defragmentation purposes. The current code accomplishes this test with a series of four if tests, but lots of jumps can be expensive in fast-path code. So Mel's patch replaces the tests with a table lookup.
There are a number of other changes along these lines - seeming micro-optimizations that one would not normally bother with. But, in fast-path code deep within the system, this level of optimization can be worth doing. The patch set also reorganizes things to make the fast path more explicit and contiguous; that, too, can speed things up, but it also helps ensure that developers know when they are working with performance-critical code.
The change which provoked the most discussion, though, was the removal of the distinction between hot and cold pages. This feature, merged for 2.5.45, attempts to track which pages are most likely to be present in the processor's caches. If the memory allocator can give cache-warm pages to requesters, memory performance should improve. But, notes Mel, it turns out that very few pages are being freed as "cold," and that, in general, the decisions on whether to tag specific pages as being hot or cold are questionable. This feature adds some complexity to the page allocator and doesn't seem to improve performance, so Mel decided to take it out. After running some benchmarks, though, he concluded that, in fact, he has no idea whether the feature helps or not. So the second version of the patch has left out the hot/cold removal, but this topic will be revisited in the future.
Mel claims some good results:
A number of standard user-space benchmarks also show improvements with this patch set. The reviews are generally good, so the chances are that these changes could avoid the lengthy delays that characterize memory management patches and head for the mainline in the relatively near future. Then there should be no excuse for trying to avoid the page allocator.
Checkpoint/restart tries to head towards the mainline
In kernel development, there is always tension between the needs of a new feature versus the needs of the kernel as a whole. Projects generally want to get their code merged as early as possible, for a variety of reasons, while the rest of the kernel community needs to be comfortable that the feature is sensible, desirable, and, perhaps most importantly, maintainable. The current push for inclusion of a feature to checkpoint and restart processes highlights this tension.
In late January, Oren Laadan posted the latest version of his
kernel-based checkpoint and restart code with the notation: "Aiming
for -mm
". There are many possible uses for checkpoints, but it is
an extremely complex problem. Laadan's current version is quite
minimal, implementing only a fairly small subset of the features
envisioned, but he would like to get the kind of review and testing that
goes along with pushing it towards the mainline.
After two weeks without much in the way of comments, another proponent,
Dave Hansen asked what, if anything, was
holding the patchset back from -mm inclusion. Andrew Morton replied that he had raised some concerns which
were "inconclusively waffled at
" a few months back.
Morton's opinion carries a fair amount of weight—not least because he
runs the targeted tree. He is looking to the future and trying to ensure
that the patches make sense:
a) end up having to merge unacceptably-expensive-to-maintain code to make it a non-toy or
b) decide not to merge the unacceptably-expensive-to-maintain code, leaving us with a toy or
c) simply cannot work out how to implement the missing functionality.
Morton asked for answers to several questions regarding what features are available in the current implementation, as well as information on what needs to be added. He also asked for indications that Laadan and Hansen had some thoughts on the design for required, but not yet implemented, features. In short, he wants to avoid any of the scenarios he outlined. In response to further questions from Ingo Molnar, Hansen outlined some of the shortcomings of the current implementation:
Hansen also had a more detailed answer to Morton's questions, which showed a lot of work still to be done. The current code only works for x86 architectures, for example, and only for basic file types, essentially just pipes and regular files. He likened the progress of checkpoint/restart to that of kernel scalability; it is a work in progress, not something that will ever be complete:
One of the main concerns is not that there is a lot still to be done, but that there may be lurking problems that either don't have solutions or can only be solved by very intrusive kernel changes. Matt Mackall looked at Hansen's list of additional features needing to be implemented and summed up the worries this way:
There is, however, a free out-of-tree implementation of checkpoint/restart
in the OpenVZ project. OpenVZ is a
virtualization scheme using its own implementation of
containers—different from that
in more recent kernels—that supports checkpointing and migrating those
containers. But it is a large patch, which Morton looked at several years
ago and concluded that it would not be welcome in the mainline. Hansen
sees OpenVZ as a useful example, but
"with all the input from the OpenVZ folks
and at least three other projects, I bet we can come up with something
better
".
An incremental approach to implementing checkpoints is reasonable, but
Morton is concerned that by merging the
current patches, the kernel developers will be
committed to merging something that looks a lot like—and is as
intrusive as—the OpenVZ patches. Molnar is more upbeat: he sees it as an important
feature without "many long-term dragons
". He does see one
potential problem area in the incremental approach, though:
That, if this feature takes off, is just a short-term worry - as basically everything will be checkpointable in the long run.
That is one of the technical issues still to be resolved with the current patchset: how does a process programmatically determine whether it is able to be checkpointed? If the process has performed some action while running on a kernel that does not support checkpointing the state caused by that action, there is a need to be able to decide that. Molnar suggested overloading the LSM security checks such that performing those actions sets a one-way "not checkpointable" flag as appropriate. That flag could be checked by the process or by some other program that was interested. Overloading the LSM hooks is not completely uncontroversial, but it does hook the kernel in many of the right places—adding an additional call to those same places for checkpointing is not likely to fly.
There was also some question about whether the "not checkpointable" flag
needs to be a one-way flag, as it could be cleared once the process has
returned to a state that is able to be checkpointed. Molnar argued that
the one-way flag is desirable: "uncheckpointable
functionality should be as
painful as possible, to make sure it's getting fixed
". Users who
run into problems checkpointing their applications will then apply pressure to
get the requisite state added to checkpoints. As a starting point,
Hansen has posted a patch that would add a
one-way flag based on the kinds of files a process had opened.
Checkpoints are a useful feature that could be used for migrating processes to different machines, protecting long-running processes against kernel crashes or upgrades, system hibernation, and more. It is a difficult problem that may never really be completely finished and it touches a lot of core kernel code. For these reasons, caution is certainly justified, but one gets the sense that some kind checkpoint/restart feature will eventually make its way into the mainline. Whether it is Laadan's version, something derived from OpenVZ, or some other mechanism entirely remains to be seen.
On the management of the Video4Linux subsystem tree
Once upon a time, the Video4Linux (V4L) development community was seen as a discordant group which hung out in its own playpen and which had not managed to implement support for much of the available hardware. Times have changed; the V4L community is energetic and productive, disruptive flame wars have all but disappeared from the V4L mailing lists, and Linux now supports a large majority of the hardware which can be found on the market. As this community moves forward, it is reorganizing things on many fronts; among other things, they are working on the creation of the first true framework for video capture devices. The V4L developers are also having to look at their code management practices; in the process they are encountering a number of issues which have been faced by other subsystems as well.The discussion started with this RFC from Hans Verkuil. Hans points out that the size of the V4L subsystem (as found under drivers/media in the kernel source) has grown significantly in recent years - it is 2.5 times larger now than it was in the 2.6.16 kernel. This growth is a sign of success: V4L has added features and support for a vast array of new hardware in this time. But it has its costs as well - that is a lot of code to maintain.
As it happens, the V4L developers make that maintenance even harder by incorporating backward compatibility into their tree. The tree run by V4L maintainer Mauro Carvalho Chehab does not support just the current mainline kernel; instead, it can be built on any kernel from 2.6.16 forward. This is not a small trick, considering that the majority of that code did not exist when 2.6.16 was released. There have been some major internal kernel API changes over that time; supporting all those kernels requires a complicated array of #ifdefs, compatibility headers, and more. It takes a lot of work to keep this compatibility structure in place. Additionally, this kind of compatibility code is not welcome in the mainline kernel, so it must all be stripped out prior to sending code upstream.
The reason for this practice is relatively straightforward: the V4L developers would like to make it possible for testers to try out new drivers without forcing them to install a leading-edge mainline kernel. This is the same reasoning that the DRM developers gave at the 2008 Kernel Summit: allowing testers to build modules for older kernels makes life easier for them. And that, in turn, leads to more testing of current code. But the cost of this compatibility is high, so Hans is proposing a few changes.
One of those would be in how the subsystem tree is managed. Currently, this tree is maintained in a Mercurial repository which represents only the V4L subsystem (it is not a full kernel tree), and which contains the backward compatibility patches. This organization makes interaction with the kernel development process harder in a number of ways. Beyond the effort required to maintain backward compatibility, the separate tree makes it harder to integrate patches written against the mainline kernel, and there is no way for this tree to contain patches which affect kernel code outside of drivers/media. Life would be easier if developers could simply work against an ordinary mainline kernel tree.
So Hans suggests moving to a tree organization modeled on the techniques developed by the ALSA project. The ALSA maintainers (who also keep backward compatibility patches) use as their primary tree a clone of the mainline git repository. Backward compatibility changes are then retrofitted into a separate tree which exists just for that purpose. By working against a mainline tree, the ALSA developers interact more smoothly with the rest of the kernel development process. The down side is that creating the backward-compatible tree requires more work; a team of V4L developers would have to commit to putting time toward that goal.
And that leads, of course, to the biggest question: what is the real value of the backward compatibility work, and how far back should the project go? There seems to be little interest in dropping compatibility with older kernels altogether; the value to testers and developers both seems to be too high. But it is not clear that it is really necessary to support kernels all the way back to 2.6.16. So, asks Hans, what is the oldest kernel that the project should support?
Hans has a clear objective here: the i2c changes which were merged for 2.6.22 create a boundary beyond which backward compatibility gets significantly harder. If kernels before 2.6.22 could be dropped, a lot of backward compatibility hassles would go away. But convenience is not the only thing to bear in mind when dropping support; one must also consider whether that change will significantly reduce the number of testers who can try out the code. It would also be good to have some sort of objective policy on backward compatibility support so that older kernels could be dropped in the future without the need for extensive discussions.
The proposed policy is this: V4L backward compatibility should support the oldest kernels supported by "the three major distros" (Fedora, openSUSE, and Ubuntu). For the moment, that kernel, conveniently, happens to be 2.6.22, which will be supported by Ubuntu 7.10 until April, 2009. (Interestingly, Hans seems to have skipped over the 6.06 "Dapper Drake" release - supported until June, 2009 - which runs a bleeding-edge 2.6.15 kernel). A quick poll run by Hans suggests that there is little opposition to removing support for kernels prior to 2.6.22.
There is some, though: John Pilkington points out:
CentOS 5 (like the RHEL5 distribution it is built from) shipped with a 2.6.18 kernel. It seems, though, that there is little sympathy for CentOS (or any other "enterprise" distribution) in the development community. Running a distribution designed to be held stable for several years and wanting the latest hardware support are seen to be contradictory goals. So it seems unlikely that the V4L tree will be managed with the needs of enterprise distributions in mind.
Thus far, no actual decisions have been made. Mauro, who as the subsystem maintainer would be expected to have a strong voice in any such decision, has not yet shown up in the discussion. Given the lack of any strong opposition to the proposals, though, it would be surprising if those proposals are not adopted in some form.
Patches and updates
Kernel trees
Architecture-specific
Core kernel code
Development tools
Device drivers
Documentation
Filesystems and block I/O
Memory management
Networking
Virtualization and containers
Benchmarks and bugs
Miscellaneous
Page editor: Jonathan Corbet
Distributions
News and Editorials
Test driving pre-releases of Ubuntu, Fedora and SimplyMEPIS
The versions used in this test drive are Ubuntu 9.04 Alpha 4, Fedora 11 Alpha and SimplyMEPIS 8 RC3. These were the current versions when this article was written. Herein you will find descriptions of the new and planned features for these popular distributions. This test drive is meant to get a better idea of how these releases are shaping up and what we can expect in the final, stable versions.
Ubuntu 9.04 Alpha 4
In addition to the regular package updates; GNOME 2.25, KDE 4.2, OpenOffice.org 3.0 and the latest, fresh versions of other popular programs — Firefox 3.0 is the default, but 3.1 is an option. Ubuntu 9.04 will be released with Linux 2.6.28.
Alpha 4 is beginning to show us how fast the new Ubuntu will boot and how nice the new notifications will look like when fully implemented. Fortunately, the Ubuntu team is producing live media during the alpha development, making testing and installation as easy as the final, stable versions.
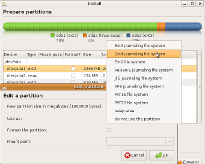
The installed system does indeed boot faster than 8.10 does, but it's still far away from Mark Shuttleworth's "blindingly quick" predictions from last September. Expectations do not always become reality, but Moblin shows us that room for improvement surely exists. As mentioned, Alpha 4 still doesn't have the planned new notification system fully implemented. A pop-up notification configuration tool offers the Ubuntu theme, but otherwise it doesn't differ from what we have seen before.
The installation now brings us support for installing ext4 partitions. Ext3 is still the default, but ext4 works like a charm, giving users a chance to try out the next generation extended file system.
The overall impression is that the current 9.04 Alpha leaves is very positive. The stability of the system is very good for an alpha version, bringing hope that 9.04 will be very nice release.
Fedora 11 Alpha
Fedora aims to be the bleeding edge leader and Fedora 11 Alpha makes this step forward by introducing btrfs support. It is still in heavy development though. A semi-functional fsck and conflicts with SELinux are the current highlights of brtfs in Fedora. Test with care. It's not available by default and requires passing the "icantbelieveitsnotbtr" test at the installation boot prompt. Fedora's GRUB still isn't able to boot either brtfs or ext4 partitions, so ext3 is still needed for the /boot partition.
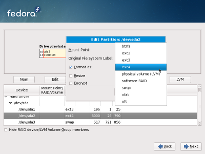
This early in the development cycle, Fedora 11 shows the current versions of software, but not much else. The new X server turns off the ctrl+alt+backspace shortcut (as does Ubuntu 9.04 Alpha 4). The new volume control system brings new usability (again, same as Ubuntu). The default desktops will be GNOME 2.26, KDE 4.2 and XFCE 4.6. Firefox is the latest 3.1 beta version which will hopefully transform into stable by the time Fedora 11 is released, which is planned for 26th of May.
Some packages from version 10 still exist and the first alpha gives us preliminary look on new system level features (file system support) and the planned software versions we should expect in 11. Upcoming pre-releases will give a better chance for deeper testing and closer estimations.
SimplyMEPIS 8 RC3
SimplyMEPIS returns to Debian after a brief affair with Ubuntu. This is the last release candidate (ed. note - the final version was released February 22). As such, this RC is very close to the final. It is based on the latest Debian release (5.0 "Lenny"). MEPIS remains loyal to KDE 3, including the 3.5.10 version.
It seems that the SimplyMEPIS team has decided to take the safe road by updating and tuning up the setup from previous releases. The installable live CD remains the only option for obtaining and installing SimplyMEPIS, making the process of installation very easy. After a few steps the installer transfers the live system to the chosen partitions in a very short time (a few minutes). Minimal activity is required from the user's perspective. Gparted may be run optionally from installer in case additional partitioning are required.
Beyond including the latest KDE 3 desktop, SimplyMEPIS developers made version 8 very fresh by including latest versions of popular programs. With rock solid Debian stable as a base, some popular programs are shipped in newer versions. This turns out to be very good practice, making MEPIS more than just a simple Debian derivative. MEPIS ships Firefox 3.0.6 (instead of Debian's Iceweasel) and OpenOffice.org 3.0 (Lenny has 2.4.1) which illustrates this practice. Those and like packages are maintained by MEPIS and stored in Debian compatible repositories. SimplyMEPIS 8 will be released with Linux 2.6.27, without Ext4 support.
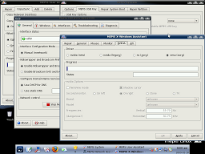
MEPIS configuration tools continue to make life easier in version 8. Probably the most interesting part of the suite is Network Assistant, which is the only option for user friendly network configuration. SimplyMEPIS 8 won't deliver Network Manager by default, but Network Assistant provides a simple interface for users who don't want to deal with shell commands for network configuration. Beside network connection management, Network Assistant provides options for additional network hardware configurations like drivers for wireless chips (ndiswrapper, Broadcom), and the possibility of switching from manual to automatic configuration (Network Manager). The rest of the administrative suite allows users to install proprietary drivers for graphic chips (Nvidia and ATI), perform X server configuration, maintain user accounts on the system, repair the boot loader and partitions, make a bootable MEPIS USB key, and do the rest of miscellaneous administrative tasks.
SimplyMEPIS 8 RC3 showed excellent stability and performance during testing. It delivers one of the fastest KDE desktops that the author ever tried. This release candidate gives very close look at what the final release will look like. It's good to see MEPIS back from a period of silence, specially with good release that 8 will be.
Final thoughts
Since SimplyMEPIS is close to the final version, it is difficult to compare to the other two. Ubuntu is ahead of Fedora at this time and Fedora does not yet give us much information about the final release. Nonetheless it's good to see that things are starting to move well in all cases.
New Releases
NexentaCore Platform 2.0 Beta2 released
NexentaCore 2.0 Beta2 has been announced. This distribution is a Debian/Ubuntu/OpenSolaris native environment based on Ubuntu 8.04 LTS (Hardy Heron).
Distribution News
Debian GNU/Linux
Appointment of new Project Secretary
Debian Project Leader Steve McIntyre introduces the new Secretary. "I'm happy to announce that Kurt Roeckx will be the new Secretary. We have spoken about the job and agreed that adding an Assistant Secretary would again be a good idea, especially given that we expect several votes to come up soon. We have therefore decided to appoint Neil McGovern again as assistant, due to his recent experience as assistant to Manoj. Thanks to both Kurt and Neil. I hope that they will cope well with their new roles."
SUSE Linux and openSUSE
An open letter to the openSUSE Community
openSUSE board members Pascal Bleser and Bryen Yunashko have sent an open letter to the community in response to worries stemming from the recent round of Novell layoffs. "Our observations over the past week convince us that Novell is still committed to the openSUSE Project. It is also our observation that the community as a whole remains active, vibrant and motivated. Our colleagues employed by Novell have assured us that while there is some frustrations and disappointment, they and the company are still as committed as ever to the openSUSE Project."
Ubuntu family
Introducing the Karmic Koala, mascot for Ubuntu 9.10
The newest member of the Ubuntu family will be the Karmic Koala aka Ubuntu 9.10. The announcement (click below) also includes information about the next Ubuntu Developers Summit (UDS) in Barcelona, May 25-29, 2009. On the server side: "A good Koala knows how to see the wood for the trees, even when her head is in the clouds. Ubuntu aims to keep free software at the forefront of cloud computing by embracing the API's of Amazon EC2, and making it easy for anybody to setup their own cloud using entirely open tools. We're currently in beta with official Ubuntu base AMI's for use on Amazon EC2."
It's a journey (ken's blog)
Ken Van Dine, the founder of Foresight Linux and an former employee of rPath has been hired by Canonical. "I will be a Desktop Integration Engineer, working on the desktop team to integrate the fine work being done by the Desktop Experience team into Ubuntu. This is a very exciting opportunity for me, I have really been doing this for the past 4 years working on Foresight Linux. Taking cool stuff people have been working on and integrating it into a distro for broader consumption."
Distribution Newsletters
Ubuntu Weekly Newsletter #130
The Ubuntu Weekly Newsletter for February 21, 2009 is out. "In this issue we cover : Ubuntu 9.10 - Karmic Koala, Announcing the Karmic Koala UDS, Jaunty feature freeze - Alpha 5 freeze ahead, Kubuntu 8.04.2 released, New Ubuntu Members - Americas Board, A Call for US LoCo Team Mentors, Next Ubuntu Hug Day, Soon: Ubuntu Weekly Newsletter in Spanish, Global Bug Jams - Michigan-South Africa-Chicago-Berlin-Florida, New Notifications for Jaunty, Meet Martin Albisetti, AJAX in Launchpad, Canonical's April Surprise - More than Ubuntu 9.04, Barcelona - Canonical discusses Ubuntu Mobile Internet Devices, Meeting Summaries - Technical Board-QA Team-US Teams, Just for Fun, and much, much more!"
Ubuntu Developer News Issue 2
The second edition of Ubuntu Developer News covers the announcement of the Karmic Koala, Jaunty Feature Freeze, Per-package uploaders and developer team structure, Python 2.6, Removal of aRts, and much more.openSUSE Weekly News, Issue 60
The openSUSE Weekly News for February 24, 2009 covers an Open Letter to the openSUSE Community, Andrew Wafaa: Ciao For Now And Bonne Chance Amigos, Lars Vogdt: Why the Buildservice is currently not for endusers, Miguel de Icaza: Mono Runtime Debugging, Jonathan_R: Getting YaST to read your own community repos and much more.The Mint Newsletter - issue 76
The The Mint Newsletter for February 24, 2009 is out with news about the release of Linux Mint 6 XFCE and other minty fresh topics.Fedora Weekly News #164
The Fedora Weekly News for February 22, 2009 is out. "This week Announcements showcases Fedora Unity respins of Fedora 10, PlanetFedora selects some great blog entries on how to tag audio streams in PulseAudio and use func, QualityAssurance explains how to participate in test days, Developments covers the "Fedora 11 Mass Rebuild", Translations describes the new "L10n Infrastructure Team", Artwork covers some pretty "Evolving Fedora 11 Artwork" and Virtualization examines attempts to bridge the gap between libvirt and host network interface configuration."
DistroWatch Weekly, Issue 291
The DistroWatch Weekly for February 23, 2009 is out. "This week we re-visit the minimal distribution install, this time with openSUSE 11.1. In the news this past week, Mark Shuttleworth announces details of the 9.10 Ubuntu release, openSUSE board members post a joint statement about the project's future in light of Novell layoffs, Red Hat signs an interoperability agreement with Microsoft, Debian project announces the appointment of a new Secretary, and NetBSD launches a desktop initiative that should bring more users to the popular cross-platform operating system. Also in the news, we introduce VirtualBSD, a FreeBSD-based desktop environment for VMware and provide a link to an animated video interview about FreeNAS, a BSD system for building network-attached storage devices. Finally, if you are an accomplished distro tester, but worry that you'll run out of new distributions to try, fear not - last week no fewer than eight new Linux distributions were submitted to DistroWatch. These include some really exotic fares, such as moonOS from Cambodia or Kongoni from South Africa. Happy distro hopping!"
Newsletters and articles of interest
The Perfect Server - Debian Lenny (Debian 5.0) (HowtoForge)
HowtoForge covers one possible way to set up a server with Debian 5.0. "This tutorial shows how to set up a Debian Lenny (Debian 5.0) server that offers all services needed by ISPs and hosters: Apache web server (SSL-capable), Postfix mail server with SMTP-AUTH and TLS, BIND DNS server, Proftpd FTP server, MySQL server, Courier POP3/IMAP, Quota, Firewall, etc. In the end you should have a system that works reliably, and if you like you can install the free webhosting control panel ISPConfig 2 (i.e., ISPConfig runs on it out of the box)."
Distribution reviews
Debian GNU/Linux 5.0: Flexible and (Almost) Free (Datamation)
Bruce Byfield takes a look at Debian GNU/Linux 5.0. "You can count on two things for every Debian release: It will be later than expected, and it will be suitable for every possible level of expertise. Debian 5.0 is no exception. Arriving almost five months later than originally scheduled, Debian 5.0 is not the most cutting-edge GNU/Linux distribution, but, like earlier releases, it is unparalleled for flexibility."
Page editor: Rebecca Sobol
Development
Bash 4.0 brings new capabilities
On February 23, 2009 version 4.0 of the BASH shell, a.k.a. the Bourne-Again SHell, was announced (see the initial LWN article for reader comments). For Linux users, at least those users who use the command line, BASH and its associated built-in commands could easily make up the most frequently run suite of Linux utilities. The BASH version 4.0 release announcement states:
A long list of new capabilities have been added to BASH, here are some of the highlights:
- The new autocd option causes bash to change to the directory that is the first word in a command.
- The new checkjobs option makes BASH report running and stopped jobs when it exits.
- New shell variables include BASHPID (the BASH process ID), COMP_TYPE (type of completion) and COMP_KEY (completion invocation character).
- BASH now supports a settable compatibility level for emulating older versions of the shell.
- New ulimit options are available for setting the socket buffer size and the number of threads.
- A new mapfile builtin can be used to populate an array with lines from a given file.
- Limited support has been added for completing command name words with globbing characters.
- The new globstar shell option allows ** to recursively match directories and files.
- The new dirspell shell option makes the filename completion code perform spelling correction on directory names.
- The read builtin's new -t option adds support for fractional timeout values.
- The new &>> redirection operator appends both standard output and standard error to a named file.
- Several new capabilities have been added to the case statement.
- New uppercase (^[^]) and lowercase (,[,]) case-modifying word expansions are available.
- Support has been added for associative array variables.
- A new coproc reserved word can specify a coprocess, which is an asynchronous command run with two pipes connected to the creating shell.
- A long list of new readline capabilities have been added.
- Much more...
The latest version of BASH has acquired some of the advanced features found in newer projects such as the Z shell and the Python language. The user experience is enhanced and new capabilities are available for those who write BASH scripts. Hopefully the backwards-compatibility considerations have been adequately dealt with. BASH 4.0 shows that even an old dog can sometimes learn a few new tricks.
System Applications
Database Software
PostgreSQL Weekly News
The February 22, 2009 edition of the PostgreSQL Weekly News is online with the latest PostgreSQL DBMS articles and resources.
Filesystem Utilities
initramfs-tools 0.93 status report
A status report has been published for initramfs-tools 0.93. "initramfs-tools is an hookable initramfs generator. It can boot on NFS, LVM2, md, LUKS, dmraid, oldstyle devices, .. The generated initramfs is generic, but can explicitly be tuned for small. It is actively deployed in Debian and Ubuntu. It is written in POSIX shell. It has an "end-user" friendly invocation with update-initramfs and the low level mkinitramfs. klibc is used for minimal initramfs. The initramfs comes together with a rescue shell. It is possible to ssh into it."
Interoperability
Samba 3.3.1 is available
Version 3.3.1 of Samba has been announced. "This is the latest stable release of the Samba 3.3 series". See the release notes for more information.
Networking Tools
conntrack-tools 0.9.11 released
Version 0.9.11 of conntrack-tools has been announced. "The netfilter project presents another development release of the conntrack-tools that includes accumulated fixes, one improvement for the polling approach and a couple of new features".
Web Site Development
Django 1.1 alpha 1 released
Version 1.1 alpha 1 of the Django web platform has been announced. "As part of the Django 1.1 release process, tonight we've released Django 1.1 alpha 1, a preview/testing package that gives a little taste of some of the new features coming in Django 1.1. As with all alpha and beta packages, this is not for production use, but if you'd like to try out some of the new goodies coming in 1.1, or if you'd like to pitch in and help us fix bugs before the final 1.1 release (due in April), feel free to grab a copy and give it a spin."
web2py 1.56.4 released
Version 1.56.4 of web2py, a Python-based web framework, has been announced. "New features In 1.56: - Authentication - Authorization (Role Based Access Controller) - CRUD - portable url fetch function - portable geocoding function - PEP8 compliant - Python 2.5 - Runs on Jython (although without db drivers) - Runs on IronPython (although without CSV, db drivers and internal web-server) - DAL shortcuts - SQLFORM has default image preview - new generic.html view - more examples and documentation - always backward compatible".
Miscellaneous
OpenHPI: 2.13.3 has been released (SourceForge)
Version 2.13.3 of OpenHPI has been announced. "Open HPI is an open source implementation of the SA Forum's Hardware Platform Interface (HPI). HPI provides an abstracted interface to managing computer hardware, typically for chassis and rack based servers."
systemtap release 0.9
Version 0.9 of systemtap, a system information gathering utility, has been announced. Many new capabilities have been added.
Desktop Applications
Audio Applications
Ardour: tempo-based time for MIDI regions
The Ardour multi-track audio workstation project has added a new capability, tempo-based time for MIDI regions. "Hi all; Ive recently done a lot of work on MIDI support (and many other things) in 3.0, and thought it might be time for an update. One often requested thing thats been missing in 3.0 is flexible tempo-based time for MIDI regions. Until recently, MIDI (like everything else in Ardour) was based on audio time. This has been reworked so the time of MIDI events is stored in tempo units everywhere, which is much nicer for working musically."
Ardour's Spanish translation ready for testing
A Spanish translation of the Ardour multi-track audio workstation has been announced. "We would like comments from as many Spanish speakers as possible, before we commit to using it in future releases of Ardour. Translation from one language to another is always a tricky process, and musical terminology - despite music "being the universal language" - varies wildly between cultures."
CAD
Kicad 2009-02-16-RC2 released
Version 2009-02-16-RC2 of Kicad, an electronic CAD application, has been announced. A number of new capabilities have been added, see the Change Log for details.Sweet Home 3D: version 1.6 released (SourceForge)
Version 1.6 of Sweet Home 3D has been announced. "Sweet Home 3D is an interior design application that helps you place your furniture on a house 2D plan, with a 3D preview... The version 1.6 provides help localized in Italian, miscellaneous enhancements and bug fixes".
Data Visualization
python-graph 1.4.2 released
Version 1.4.2 of python-graph has been announced, it includes a bug fix. "python-graph is a library for working with graphs in Python. This software provides a suitable data structure for representing graphs and a whole set of important algorithms."
Desktop Environments
compiz 0.8.0 announced
Version 0.8.0 of compiz, a composite window manager, is out. Changes include: "New plugin "commands" that handles the bindings for arbitrary commands that previously were handled in core. In addition to the previously present key bindings button and edge bindings were added as well. New plugin "gnomecompat" which handles bindings that are exclusively used in the Gnome desktop environment and removed the corresponding bindings from core. This change fixes main menu and run dialog bindings for KDE users as those previously were conflicting between compiz and KDE. Gnome users upgrading should make sure to enable this plugin..."
GNOME 2.25.91 beta released
Beta version 2.25.91 of the GNOME desktop environment has been released. "This is the seventh development release, and the second beta, towards our 2.26 release that will happen in March 2009. By now most things are in place, and your mission is easy: Go download it. Go compile it. Go test it. And go hack on it, document it, translate it, fix it."
GNOME Software Announcements
The following new GNOME software has been announced this week:- Brasero 2.25.91.2 (bug fixes and translation work)
- Clutter 0.8.8 (bug fixes)
- Clutter-GTK 0.8.3 (bug fixes and documentation work)
- ghex 2.24.0 (bug fixes, documentation and translation work)
- glibmm 2.19.3 (new features and bug fixes)
- gstreamermm 0.10.0 (new features and bug fixes)
- gthumb 2.10.11 (new features, bug fixes and translation work)
- libgee 0.1.5 (new feature)
- libgnomekbd 2.25.91 (bug fixes)
- Orca 2.24.4 (bug fixes)
- PyGobject 2.16.1 (bug fixes and license change)
- Rygel 0.2.2 (new features and bug fixes)
- Vala 0.5.7 (new features and bug fixes)
- Vala Toys for gEdit 0.4.0 (new features and bug fixes)
- Vala Toys for gEdit 0.4.1 (bug fix)
KDE Software Announcements
The following new KDE software has been announced this week:- 2ManDVD 0.3 (new features, bug fixes and translation work)
- 2ManDVD 0.4 (new features and bug fixes)
- Babiloo 2.0 (new features and translation work)
- ConvertAudio 0.0 (initial release)
- Frescobaldi 0.7.6 (new features)
- German Radio Streams Service 0.10 (new features)
- KDE CDEmu Manager 0.1 (initial release)
- kdesvn 1.2.4 (bug fixes)
- kikkanji 1.0 (unspecified)
- Kim 0.9.5 (KDE4 support)
- KMyMoney 0.9.3 (new features, bug fixes and translation work)
- KRadio for KDE4.x snapshot-2009-02-19 (new features and bug fixes)
- KRadio4 for KDE4.x snapshot-2009-02-20 (new features and bug fixes)
- Kvm 0.2.2 (bug fix)
- libkdcraw 0.1.8 (unspecified)
- Opeke 0.4 (new features)
- QTrans 0.2.1.4-3 (new feature)
- Soprano 2.2.2 (bug and build fixes)
- Wally 2.0.0 (new features, bug fixes and code rewrite)
Xorg Software Announcements
The following new Xorg software has been announced this week:- libdrm 2.4.5 (new features and bug fixes)
- libXfont 1.4.0 (bug fixes and code cleanup)
- randrproto 1.2.99.4 (new features and bug fixes)
- xf86-input-acecad 1.3.0 (bug fixes, code cleanup and documentation work)
- xf86-input-aiptek 1.2.0 (bug fixes and code cleanup)
- xf86-input-penmount 1.4.0 (bug fixes and code cleanup)
- xf86-input-void 1.2.0 (code cleanup and documentation work)
- xf86-video-ati 6.11.0 (new features, bug fixes and code cleanup)
- xf86-video-glide 1.0.2 (bug fixes, code cleanup and documentation work)
- xf86-video-intel 2.6.2 (bug fixes and code cleanup)
- xf86-video-rendition 4.2.1 (code cleanup)
- xf86-video-sisusb 0.9.1 (bug fixes and code cleanup)
- xf86-video-voodoo 1.2.1 (bug fixes and code cleanup)
Financial Applications
GnuCash 2.2.9 Released
Version 2.2.9 of GnuCash has been announced. "The GnuCash development team proudly announces GnuCash 2.2.9 aka "Mirror-like", the ninth bug fix release in a series of stable releases of the GnuCash Free Accounting Software."
KMyMoney 0.9.3 released
Version 0.9.3 of KMyMoney has been announced. "The KMyMoney Development Team is proud to announce the immediate availability of version 0.9.3 of "the BEST personal finance manager for FREE users". This offers many new features and improvements over the existing, stable, 0.8 series; and the previous development version 0.9".
Geographical Software
NovaRS: 1.3.1 is out (SourceForge)
Version 1.3.1 of NovaRS has been announced. "NovaRS is a GNSS station controlling software, which supports NovAtel GPS/GLONASS receivers (OEMV3, OEM4). Added automatic leap seconds setup. Debian/Ubuntu repository is repaired."
GUI Packages
wxPython 2.8.9.2 released
Version 2.8.9.2 of wxPython, a python interface to the wxWindows GUI toolkit, has been announced. "The wxWidgets team is in the early stages of preparing for a 2.8.10 release, but I already had a set of 2.8.9.2 release candidate files that I made a few days ago. Since it's still possible that there could be delays in the 2.8.10 release I thought that it would be nice to go ahead and release the 2.8.9.2 binaries."
Medical Applications
Freemed-YiRC V1.10 released (LinuxMedNews)
LinuxMedNews covers the release of Freemed-YiRC 1.10. "Freemed-YiRC V1.10 has been officially released. The major news is this new release incorporates foster care/adoption/respite functionality, increasing the scope of FMYiRC beyond just Youth in Residential Care. Other major new features include PDF creation capability, as well as a much improved calendaring system (with internal e-mail alert capability)."
OpenSource LIS - Laboratory Information System (LinuxMedNews)
LinuxMedNews has announced the OpenELIS project. "OpenELIS is a robust Enterprise Laboratory Information System built around an extensible and scalable framework. OpenELIS is designed and developed through the collaborative efforts of Public Health Laboratories to accommodate business processes that are common to all public health laboratories; encompassing clinical, environmental, newborn screening, and animal testing."
Multimedia
Elisa Media Center 0.5.29 released
Version 0.5.29 of Elisa Media Center has been announced. "This release is a "light weight" release, which means it is supposed to be pushed to the users through our automatic plugin update system. That is why there is no new Elisa installer nor any new packages from our side".
Peer to Peer
MLDonkey: New release 3.0.0 (SourceForge)
Version 3.0.0 of MLDonkey has been announced. "MLDonkey is a multi-platform multi-network peer-to-peer client. This is an urgent security update, it will also reduce CPU and memory usage due to optimized storage of the IP blocklist."
Miscellaneous
Animal Shelter Manager: 2.3.6 released (SourceForge)
Version 2.3.6 of Animal Shelter Manager has been announced. "Animal Shelter Manager is a complete computer solution for animal sanctuaries and shelters. Features complete animal management, document generation, full reporting, charts, internet publishing, pet search engine integration and more. This release adds easy networking support for existing users with local databases, diagnostic for fixing broken codes in historical data, much improved applet functionality and support for Windows 95 and 98."
BleachBit 0.4.0 released
Version 0.4.0 of BleachBit has been announced. "BleachBit is a Internet history, locale, registry, privacy, and temporary file cleaner for Linux on Python v2.4 - v2.6. Notable changes for 0.4.0: * Introduce CleanerML, a system for creating cleaners in XML. * Add cleaners for aMSN, CrossOver Chromium (Google Chrome), ELinks, emesene, GL-117, Hippo OpenSim Viewer, Midnight Commander, Recoll, Rhythmbox, Tremulous, Vuze (formerly Azureus), and WINE. * Update Bulgarian, French, and Spanish translations. * Add Russian translation."
OpenSSH 5.2 released
Version 5.2 of OpenSSH has been announced. "The focus of this release has been on bugfixes as the previous openssh-5.1 release introduced many new features and made some invasive changes."
Languages and Tools
Caml
Caml Weekly News
The February 24, 2009 edition of the Caml Weekly News is out with new articles about the Caml language.
Python
Hypy 0.8.3 released
Version 0.8.3 of Hypy has been announced. "All my fans of detailed example documentation are gonna love this release. If you've been wondering whether Hypy has the feature you want for your searching, check out the examples page and see for yourself. Hypy is a fulltext search interface for Python applications. Use it to index and search your documents from Python code. Hypy is based on the estraiernative bindings by Yusuke Yoshida."
Miros: a hierarchical state machine module
The Miros for Python project has been announced. "Miros is a module that implements a Hierarchical State Machine (HSM) class (i.e. one that implements behavioral inheritance). It is based on the excellent work of Miro Samek (hence the module name "miros"). This implementation closely follows an older C/C++ implementation..."
pytemplate 1.5: template for python developers
Version 1.5 of pytemplate has been announced. "I'm pleased to announce the new release (1.5) of pytemplate project, major step in its young life. pytemplate project is a framework helping python developers at starting their program with a lightweight template, managing basic options like configuration file, logging, daemon capabilities, signal management. I believe that this project is able to help to bring development quality and speed leverage to a lot of small programs."
Tcl/Tk
Tcl-URL! - weekly Tcl news and links
The February 19, 2009 edition of the Tcl-URL! is online with new Tcl/Tk articles and resources.
XML
Announcing py-dom-xpath, a pure Python XPath implementation
The py-dom-xpath project has been announced. "py-dom-xpath is a pure Python implementation of XPath 1.0. It supports almost all XPath 1.0, and works well with xml.dom.minidom."
IDEs
Pydev 1.4.4 released
Version 1.4.4 of Pydev, an Eclipse IDE plugin for Python and Jython, has been announced. "This release fixes a critical bug when configuring the interpreter (if no environment variables were specified, it was not possible to configure an interpreter)".
Profilers
line_profiler and kernprof 1.0b2 announced
Version 1.0b2 of line_profiler and kernprof has been announced. "line_profiler is a module for doing line-by-line profiling of functions. kernprof is a convenient script for running either line_profiler or the standard library's cProfile module."
Page editor: Forrest Cook
Linux in the news
Companies
HP joins the Ubuntu Linux bandwagon (betanews)
betanews covers HP's new support for the Ubuntu distribution on its servers. "HP's Linux support will no longer be limited to Red Hat and SuSE Linux. Through a new partnership with Canonical, HP is becoming one of the latest in a series of huge IT players to hop aboard the Ubuntu Linux bandwagon. More specifically, HP and Linux distributor Canonical are now working toward full certification of Ubuntu on HP Proliant servers, according to Mark Murphy, Canonical's alliances manager."
Business
An open source to a brighter future? (TimesOnline)
TimesOnline looks at the business success of open source software. "Martin Michlmayr, a former project leader for Debian, an open source operating system, argues: "Open source is not a lawless frontier at all. There are clear license terms that have to be followed, even though open source generally offers more freedoms than proprietary software. It's true, that many organisations are still struggling to understand open source and its license terms. That's why Hewlett Packard, together with other partners, started a open source governance community, FOSSBazaar, to share best practices.""
Linux Adoption
Can Cellphones Grow Up to Rival PCs? (New York Times)
The New York Times analyzes the changing computer landscape. "What about Linux, which many users found hard to use and not compatible with all the programs they want to run? There has not been a substantial incentive for a user to choose Linux before, Mr. Burchers answered. If you say a netbook is almost half the thinness, the battery life is four times, and it costs 100 bucks less, but I have to use Linux, that is an incentive. Linux, he added, is improving. This has been the first generation that is for non-geeks."
Interviews
Mozilla interview: Opening up mobile browsing (The H)
The H (formerly known as Heise) talks with Mozilla VP Jay Sullivan about mobile browsing. "One of the reasons that the browser that comes out of the Fennec project will be called Firefox, rather than Firefox Mobile, is that there are far fewer differences between the desktop and mobile world than you'd expect. Location on the PC might come from a Wi-Fi service, rather than GPS or cell tower location, but it's still useful for searches, and cameras are becoming common on notebooks. Beyond telephony and SMS, Sullivan says there are few unique mobile features. 'As we look into it, every time we think we've found a feature, that's kind of a mobile feature, we say that should be in Firefox too.'"
Interview with Jimmy Wales (ODBMS Industry Watch)
Marco Dettweiler and Roberto V. Zicari interview Jimmy Wales, President of Wikia, Inc.; Board member and Chair Emeritus of the Wikimedia Foundation. "Q. How does it compare Wikia with Wikipedia? I would say, it's the rest of the Library, it is everything that does not belong to an Encyclopedia. For example, Uncyclopedia is a humor site, it is a parody of Wikipedia, it is not a serious site, it is all a joke. Another example, we have a site about Wikia Green , which is all about sustainable living, it is not a neutral site, it is specifically advocating for specific prospective in the world."
Resources
Anatomy of ext4 (developerWorks)
developerWorks has posted a detailed look at the ext4 filesystem. "One of the first visible differences in ext4 is the increased support for file system volumes, file sizes, and subdirectory limits. Ext4 supports file systems of up to 1 exabyte in size (1000 petabytes). Although that seems huge by today's standards, storage consumption continues to grow, so ext4 was definitely developed with the future in mind. Files within ext4 may be up to 16TB in size (assuming 4KB blocks), which is eight times the limit in ext3."
OpenOffice.org Base: Creating basic databases and tables (Linux Journal)
Bruce Byfield introduces OpenOffice.org Base on Linux Journal. "When databases became available for the personal computer in the mid-1980s, they quickly gained a mystique as the ultimate productivity applications. Despite their widespread use, in some ways they have never lost that mystique -- so much so that many desktop users will stretch the use of spreadsheets to cumbersome lengths rather than consider setting up a database. Fortunately, OpenOffice.org Base makes setting up a database easy, giving you a more efficient way of handling data than a spreadsheet."
Reviews
ACCESS Linux Platform 3.0 unveiled (ars technica)
Ars Technica covers the release of the Access Linux Platform 3.0. "ALP was developed by PalmSource, a software company that split from Palm in 2003 and was subsequently acquired by ACCESS in 2005. ALP's PalmSource legacy makes it sort of a spiritual successor to the original PalmOS, but it's important to note that ACCESS is not related to Palm and that ALP is not related in any way to the Linux-based platform that Palm is developing today."
A developer's introduction to Google Android (ars technica)
There is a lengthy introduction to the Android platform on ars technica. "A look at the Dalvik source code reveals that it is largely derived from the Harmony project, an open source Java implementation that is distributed under the Apache license and is maintained under the umbrella of the Apache Foundation. Android also leverages Harmony's class library. Google optimized various components of Harmony in several key ways. In addition to adapting the Harmony VM to support Dex, Google also rewrote parts of the stack to use faster native libraries-such as ICU for character encoding and OpenSSL for encryption."
HP's Mini 1000 Mi Takes Netbooks a Big Step Forward (Business Week)
Business Week takes a look at the HP Mini Mi. "The Mi doesn't try to replace a standard PC. It is not aimed at people who use Microsoft Outlook for corporate e-mail, create documents in Word, run spreadsheets, edit photos or video, or prepare presentations on their computers. Like all netbooks, it is designed for Web browsing and consuming information, not creating it. When you fire it up, the initial screen gives you a summary of your e-mail in-box, favorite Web links, and access to photos and music stored on the computer. A button at the bottom of the screen lets you use other installed programs, which are displayed as big icons sorted into tabs such as "Internet" and "media." The designers were careful not to cram lots of unnecessary information onto the home screen. They also kept navigation simple and made sure the choices are presented clearly."
Marvell's Plug Computer: A tiny, discrete, fully functional 5 watt Linux server (TG Daily)
TG Daily takes a look at a really small computer. "Marvell announced today a new type of computer. It's about the size of an AC to DC converting wall outlet plug, but is really a full SoC with a 1200 MHz CPU, built-in 512 MB Flash, 512 MB DRAM, Gigabit Ethernet and USB 2.0 support. It runs small versions of Linux, consumes about 5 watts max while allowing remote users (presumably those authorized by the owner) to access data stored on the device from remote locations including local intranets or over the Internet. The $49 device opens up a wide array of extremely low-power, low-volume, always on applications."
X Server 1.6.0 Has Been Released (Phoronix)
Phoronix notes the X server 1.6.0 release. "X Server 1.6 introduces the server bits for Direct Rendering Infrastructure 2 (the 3D bits can already be found in Mesa and the Intel driver), X Input 1.5 with device properties, Predictable Pointer Acceleration, and RandR 1.3. Beyond those key features, there are also a number of bug-fixes, EXA improvements, and various other improvements."
Miscellaneous
Could the Linux Foundation get too big? (ZDNet blog)
Dana Blankenhorn wonders if the Linux Foundation could get too big, just as MIPS Technologies joins the group. "[MIPS] said most of its developers are already using Linux. Fair enough. But this got me wondering whether it's possible for the Linux Foundation to get too big. Oracle is already a platinum member, Cisco a gold, Dell a silver. What if Microsoft wanted in? Or Apple?"
Page editor: Forrest Cook
Announcements
Non-Commercial announcements
FSF announces EndSoftwarePatents.org phase II
The Free Software Foundation has announced funding for a new phase of the End Software Patents project. To that end, it is creating a catalog of studies, arguments, and legal analyses for use by those seeking to kill software patents. "For this new phase of End Software Patents work, the FSF has engaged veteran anti-software-patent lobbyist Ciaran O'Riordan, taking over from Ben Klemens as director of ESP. O'Riordan brings years of experience campaigning against software patents in the EU. This knowledge, combined with what was learned during the Bilski work, will form the starting point for a global information resource and campaign. The goal is make it easy for activists around the world to benefit from existing knowledge, often scattered and sometimes disappearing with time." Click below for the full announcement.
Linux Foundation Newsletter
The February, 2009 edition of the Linux Foundation Newsletter has been published. "In this month's Linux Foundation newsletter: * Collaboration Summit Agenda Announced * LinuxCon Call for Papers * New Style Connects Foundation Web Sites * "We're Linux" Video Contest Still Going Strong * Linux Foundation in the News * From The Director"
Two Linux Fund press releases
The Linux Fund has announced a partnership with Inkscape developer Milosz Derezynski and an expansion of its board of directors. Click below for both press releases.
Commercial announcements
Red Hat Sets Its Virtualization Agenda (Red Hat press release)
Red Hat has announced its virtualization strategy, which is based on moving away from Xen to KVM. "Red Hat's strategic direction for the future development of its virtualization product portfolio is based on KVM, making Red Hat the only virtualization vendor leveraging technology that is developed as part of the Linux operating system. Existing Xen-based deployments will continue to be supported for the full lifetime of Red Hat Enterprise Linux 5, and Red Hat will provide a variety of tools and services to enable customers to migrate from their Red Hat Enterprise Linux 5 Xen deployment to KVM."
World of Goo available for Linux
A Linux port of the commercial game World of Goo has been announced. It is DRM free and available for 64 bit systems as well as 32 bit systems.* More copies of the game were sold via our website on the day the Linux version released than any other day. This day beat the previous record by 40%. There is a market for Linux games after all :)
New Books
Java Web Services: Up and Running - New from O'Reilly
O'Reilly has published the book Java Web Services: Up and Running by Martin Kalin.
Resources
Coverity announces open-source application analysis site
Coverity has announced its new scan.coverity.com, which analyzes over 2500 open-source projects. "As an outgrowth of its contract with the U.S. Department of Homeland Security (DHS), Coverity collected this data via the Scan site using the Coverity Architecture Analyzer product. This new, publicly accessible resource includes application architecture files and generated diagrams that will benefit developers planning to incorporate open source packages in their applications, as well as developers that want to learn the architectures of successful projects to improve the structure of their own applications."
Education and Certification
Free Technology Academy set up
A new European Free Technology Academy has been launched. "A Consortium formed by three universities and led by the Free Knowledge Institute (FKI) has received the support from the EC's Lifelong Learning Programme to offer an international educational programme on Free Software. Following the Open Educational Resources movement, all learning materials will be freely available through the Internet. The use of Free Software (also referred to as Open Source software or Libre Software) is expanding rapidly in governmental and private organisations."
Calls for Presentations
CFP: EuroBSDCon 2009 - Cambridge, UK
A call for papers has gone out for EuroBSDCon 2009. The event will take place in Cambridge, UK on September 18-20, submissions are due by May 31. "The ninth European BSD conference is a great opportunity to present new ideas to the community and to meet some of the developers behind the different BSDs. The two day conference program (September 19 - 20) will be complemented by a tutorial day preceding the conference (Sept 18)."
Upcoming Events
DebConf10 to be in New York City
The announcement has gone out: DebConf10 will be held in New York City at an unspecified time in 2010. "In eleven years of DebConf history, this will be the first time that the Debian developer conference takes place in the United States of America, which had been avoided in previous years due to visa and other immigration issues. The NYC team had addressed those issues from the very start and submitted a very convincing bid."
Only one week left to register for FOSS Health 09 at earlybird rates (LinuxMedNews)
LinuxMedNews has posted a reminder that FOSS Health 09 early-bird registration ends this week. "This is the last week to register for FOSS Health 09 for the early-bird rate! It costs only $60 to register now, but it will change to $250 for later registration. This rate is specifically intended so that individual community members can attend cheaply." The event will be held in Houston, TX on July 31 - Aug 2.
Events: March 5, 2009 to May 4, 2009
The following event listing is taken from the LWN.net Calendar.
| Date(s) | Event | Location |
|---|---|---|
| March 3 March 8 |
CeBIT 2009 | Hanover, Germany |
| March 4 March 7 |
DrupalCon DC 2009 | Washington D.C., USA |
| March 6 | Dutch Perl Workshop | Arnhem, The Netherlands |
| March 7 | Ukrainian Perl Workshop 2009 | Kiev, Ukraine |
| March 8 March 11 |
Bossa Conference 2009 | Recife, Brazil |
| March 9 March 13 |
Advanced Ruby on Rails Bootcamp with Charles B. Quinn | Atlanta, GA, USA |
| March 9 March 12 |
O'Reilly Emerging Technology Conference | San Jose, CA, USA |
| March 12 March 15 |
Pingwinaria 2009 - Polish Linux User Group Conference | Spala, Poland |
| March 14 | OpenNMS User Conference (Europe) 2009 | Frankfurt Main, Germany |
| March 14 March 15 |
Chemnitzer Linux Tage 2009 | Chemnitz, Germany |
| March 16 March 20 |
Android Bootcamp with Mark Murphy | Atlanta, USA |
| March 16 March 20 |
CanSecWest Vancouver 2009 | Vancouver, BC, Canada |
| March 18 | Linuxwochen Österreich - Klagenfurt | Klagenfurt, Austria |
| March 21 March 22 |
Libre Planet 2009 | Cambridge, MA, USA |
| March 23 March 27 |
iPhone Bootcamp | Atlanta, Georgia, USA |
| March 23 April 3 |
Google Summer of Code '09 Student Application Period | online, USA |
| March 23 March 27 |
ApacheCon Europe 2009 | Amsterdam, The Netherlands |
| March 24 March 26 |
UKUUG Spring 2009 Conference | London, England |
| March 25 March 29 |
PyCon 2009 | Chicago, IL, USA |
| March 27 March 29 |
Free Software and Beyond The World of Peer Production | Manchester, UK |
| March 28 | Open Knowledge Conference 2009 | London, UK |
| March 31 April 2 |
Solutions Linux France | Paris, France |
| March 31 April 3 |
Web 2.0 Expo San Francisco | San Francisco, CA, USA |
| April 3 April 5 |
PostgreSQL Conference: East 09 | Philadelphia, PA, USA |
| April 3 April 4 |
Flourish Conference | Chicago, IL, USA |
| April 6 April 8 |
CELF Embedded Linux Conference | San Francisco, CA, USA |
| April 6 April 7 |
Linux Storage and Filesystem Workshop | San Francisco, CA, USA |
| April 8 April 10 |
Linux Foundation Collaboration Summit | San Francisco, CA, USA |
| April 14 | OpenClinica European Summit | Brussels, Belgium |
| April 15 | Linuxwochen Österreich - Krems | Krems, Austria |
| April 16 April 17 |
Nordic Perl Workshop 2009 | Oslo, Norway |
| April 16 April 19 |
Linux Audio Conference 2009 | Parma, Italy |
| April 16 April 18 |
Linuxwochen Austria - Wien | Wien, Austria |
| April 20 April 24 |
samba eXPerience 2009 | Göttingen, Germany |
| April 20 April 23 |
MySQL Conference and Expo | Santa Clara, CA, USA |
| April 20 April 24 |
Perl Bootcamp at the Big Nerd Ranch | Atlanta, GA, USA |
| April 20 April 24 |
Cloud Slam '09 | Online, Online |
| April 22 April 25 |
ACCU 2009 | Oxford, United Kingdom |
| April 23 April 26 |
Liwoli 2009 | Linz, Austria |
| April 23 | Linuxwochen Austria - Linz | Linz, Austria |
| April 23 April 24 |
European Licensing and Legal Workshop for Free Software | Amsterdam, The Netherlands |
| April 25 May 1 |
Ruby & Ruby on Rails Bootcamp | Atlanta, Georgia, USA |
| April 25 April 26 |
LinuxFest Northwest 2009 10th Anniversary | Bellingham, Washington, USA |
| April 25 | Linuxwochen Austria - Graz | Graz, Austria |
| April 25 | Festival Latinoamericano instalación de Software libre | All Latin America, All Latin America |
| April 25 | Grazer Linux Tage 2009 | Graz, Austria |
| April 27 | OSDM 2009 | Bangkok, Thailand |
If your event does not appear here, please tell us about it.
Audio and Video programs
Ignite launches weekly video series highlighting the best of geek culture
O'Reilly has announced the launch of the Ignite Show. ""Enlighten us, but make it quick" is the slogan of Ignite--a community event celebrating the passion and creativity of geek culture, sponsored by O'Reilly Media. Ignite events showcase a series of speakers who, in rapid succession, give five-minute talks on whatever ignites their passion. The format is half the fun with Ignite--speakers are allowed 20 slides that auto-forward every 15 seconds, whether they're ready or not. Organized by volunteers in the local geek community and presented free of charge to their communities, Ignite talks range from "How to Buy a Car" to "Hacking Chocolate" to "Transhuman Technology Trends.""
Page editor: Forrest Cook

